Paul Melcher
Head of Business Development, Imatag
In today’s economy, it is impossible to sell products or services without using pictures or videos. In some spaces, like e-commerce, pictures are the product.
By capturing and diverting official product images, counterfeiters and grey marketers can seize a substantial size of a brand’s market, regardless of their counterfeiting ability, simply because consumers make their purchasing decision solely based on the product’s image (Finney and Yip, 2019). By the time they pay and receive it, it is too late.
Brands need to produce and distribute numerous images to fulfill market needs. Each product put on the market needs at least three photos from various angles to properly display the product for potential buyers. In the process, between the moment the photo is shot to when it finally lands on a web page, the photo will have been passed around extensively. Accordingly, ill-intended players have many opportunities to intercept and misuse them. There are two critical moments:
Pre-launch: This is the period when teams are busy preparing for the official, public launch. There is increasing exchange activity between groups, and for the first time, product images have to be shared with external vendors; be it a printer, to prepare for Point of Sale (POS) signage, a marketing firm, for communication execution, distributors and vendors, to get ready for the launch date. Each time, there is an opportunity for someone in the chain to break the trust and copy an image. That copy can end up on a public website or be shared directly with a counterfeiter. It doesn’t matter if this is pure negligence or intentional: the damage is done. The product is leaked, resulting in painfully lost sales, and in some cases, counterfeited products can hit the market before the official product launch.
After launch: With multiple copies of high-quality product images now freely available everywhere, it is a breeze for anyone to use them with nefarious intent. And while most re- usages are innocent, some have clear consequences to a brand’s revenue. How better to promote and sell a counterfeited version of a product than by using legitimate, brand-produced product images?
In both cases, it is the brand’s own content that is used against itself. The good news is that there are remedies.
While invisible watermarking has been around for a while, its usage had primarily been limited to protecting big Hollywood movies. Not anymore. By manipulating pixels ever so slightly, this technology can imperceptibly turn images into snitches–the good kind (see Figure 1).
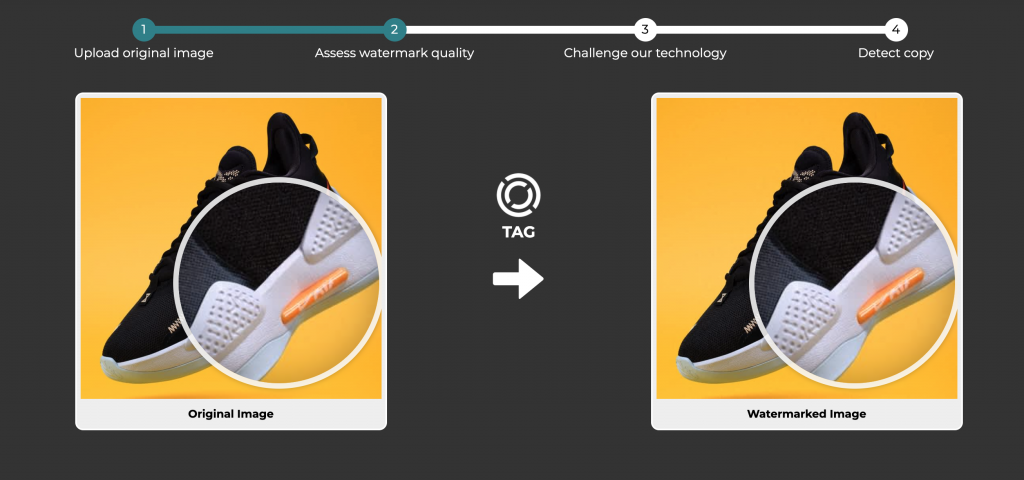
Figure 1: Invisible watermarking turns product images into brand-friendly snitches
In the scenario of a pre-launch, each copy of the same image sent out has its unique marking tied to a specific recipient. If and when the image is found publicly or in unapproved usage, a simple reading of the watermark reveals who facilitated it. From a necessary relationship termination to seeking monetary damages, a brand can then take appropriate action.
Associating invisible watermarking to random website monitoring vastly increases the chances of catching misuse (imatag, 2019). A brand can safely post their product images on their website, knowing that they will be automatically notified if and when any usage is found.
Some brands choose to strengthen the power of this technology by registering their assets with the US Copyright Office, allowing them to use the full force of infringement legislation against the violators. Others use it as a powerful deterrent, clearly communicating to recipients beforehand that any prohibited usage of the files shared with them will be identified and easily traceable to its source.
While visual assets are the core of brand sales and marketing, they can also become the most effective weapon of a powerful brand protection strategy.
THE BRAND PROTECTION PROFESSIONAL |JUNE 2021 | VOLUME 6 NUMBER 2
2021 COPYRIGHT MICHIGAN STATE UNIVERSITY BOARD OF TRUSTEES
THE BRAND PROTECTION PROFESSIONAL |DECEMBER 2017 | VOLUME 2 NUMBER 4
2017 COPYRIGHT MICHIGAN STATE UNIVERSITY BOARD OF TRUSTEES